Vulnerability Response
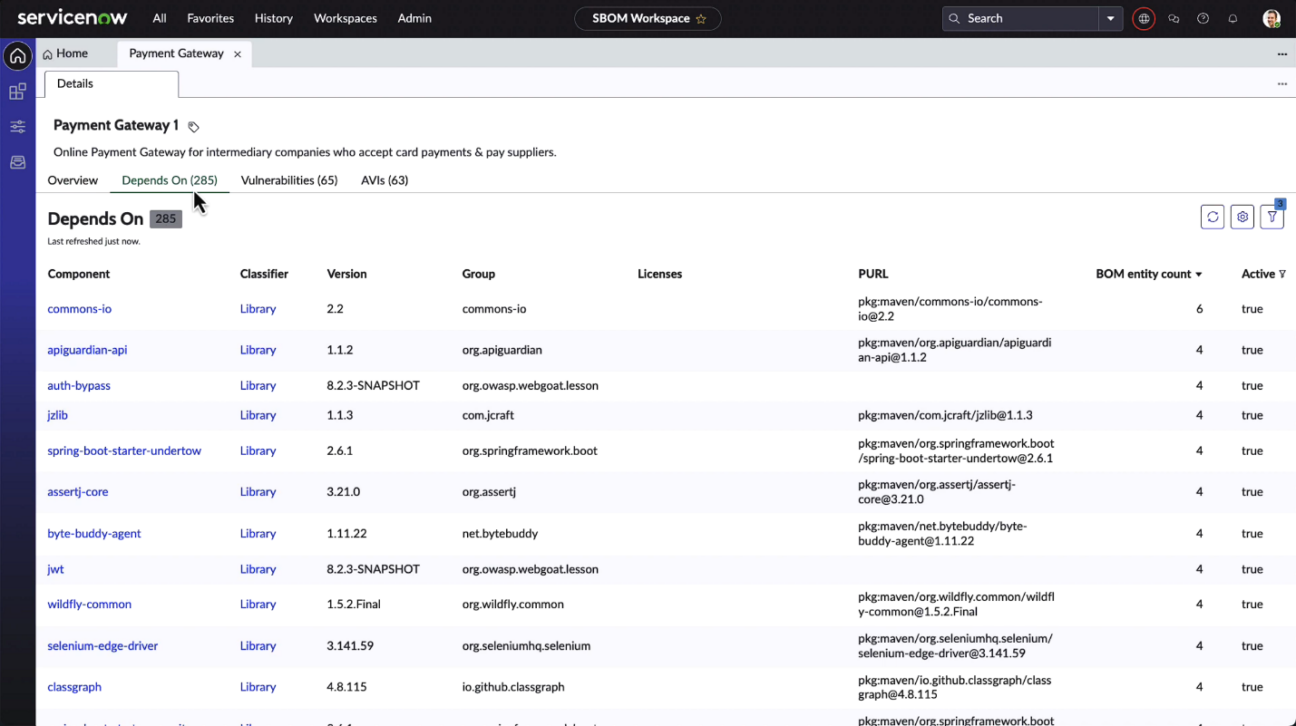
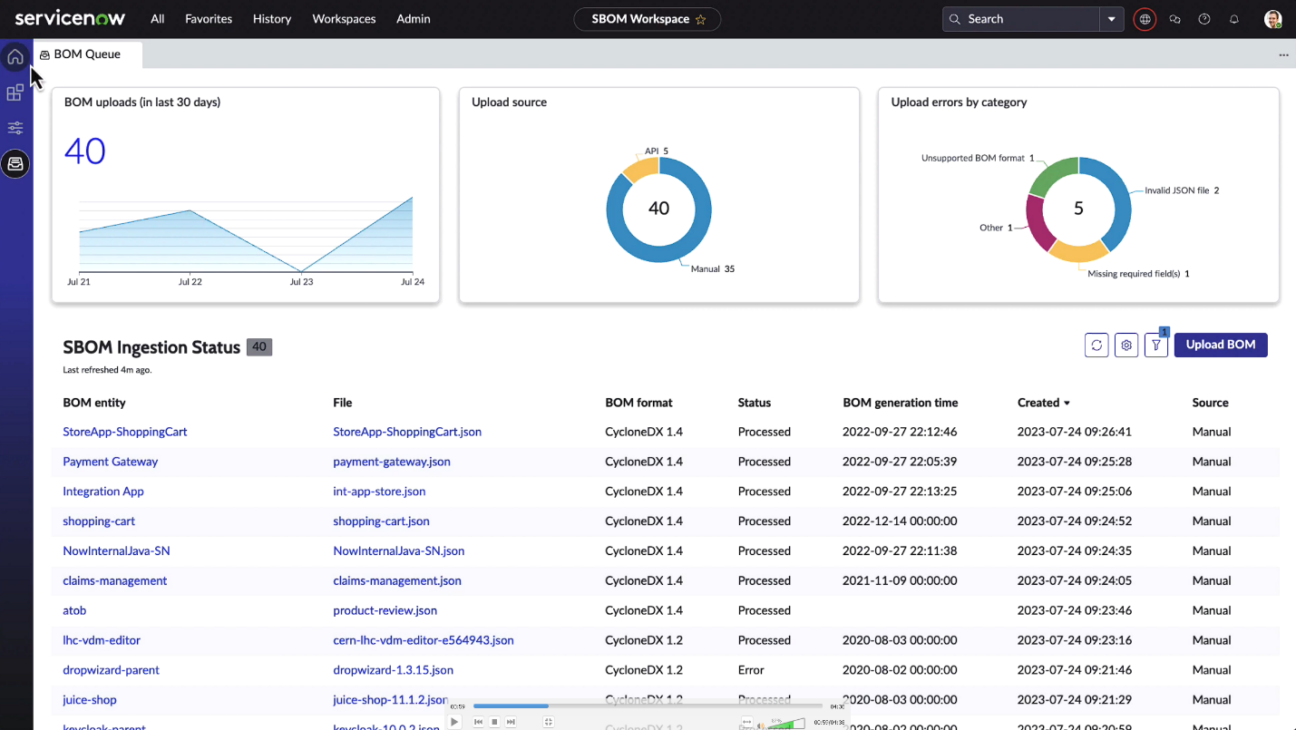
Software Bill of Materials (SBOM)
The Software Bill of Materials (SBOM) is a detailed catalogue of all software components and serves as an integral tool akin to an ingredient list. With the increasing reliance on third-party and open-source software, understanding your software’s makeup has become more crucial than ever.
Incidents like the SolarWinds breach and the Log4j vulnerability underscore the importance of this comprehension. The ServiceNow Vancouver release champions this feature by aligning with industry standards like CycloneDX and SPDX.
Acknowledged by the National Telecommunications and Information Administration (NTIA) and underscored by the U.S. Executive Order in 2021, the SBOM concept has gained traction, particularly for federal bodies and their associates. Additionally, with the European Union’s introduction of the Cyber Resilience Act in 2022, the emphasis on having a detailed software inventory has become even more pronounced on a global scale.
By offering a clear component list, businesses can bolster transparency and trust. Furthermore, the ServiceNow Software Bill of Materials enables rapid identification of known vulnerabilities, enhancing response times. Such transparency not only ensures security but also compliance with evolving global regulations.
For software teams, the Software Bill of Materials is invaluable, aiding in seamless integration and ensuring compatibility during software updates.
Atlassian Jira Integration
The ServiceNow Vancouver release introduces refined integration with Atlassian Jira. Through daily scheduled jobs, it ensures bi-directional synchronisation between Jira and Vulnerability Response for real-time updates. This synergy not only bolsters comprehensive visibility for remediation users and vulnerability managers but also strengthens enterprise-wide cybersecurity resilience.
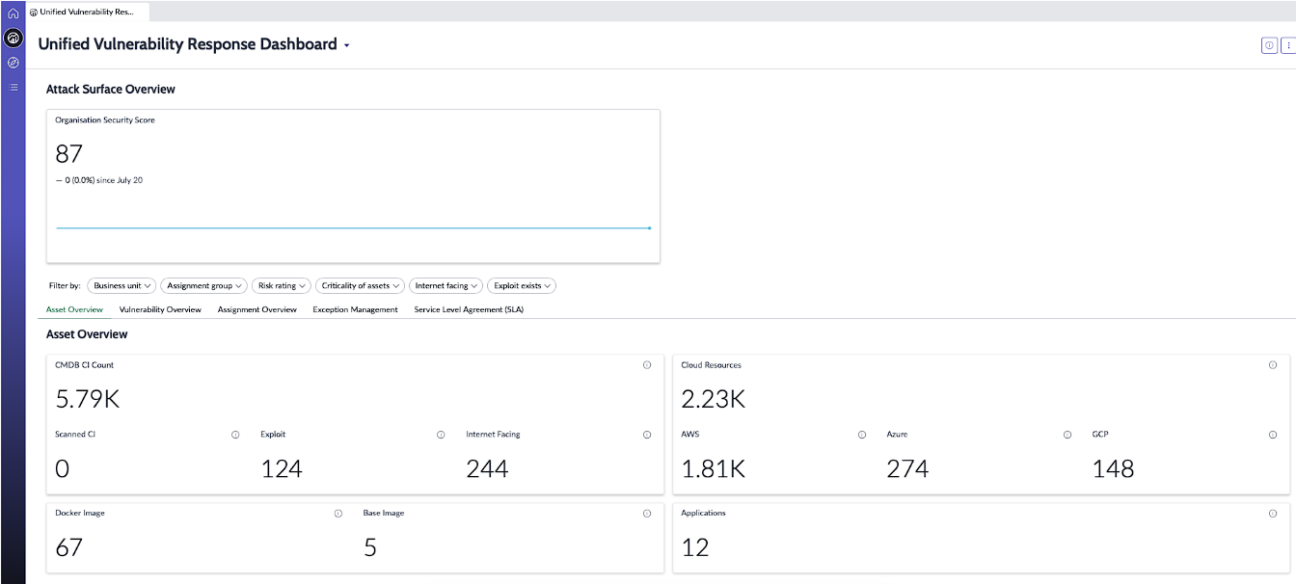
Unified Attack Surface Dashboard
The Unified Vulnerability Response Dashboard emerges as a crucial tool for modern cybersecurity. It provides a comprehensive view of an organisation’s threat landscape, consolidating vulnerability data from infrastructure, cloud, applications, and more. It offers deeper insights into assets, highlighting external-facing entities and unscanned items.
Centralised data access is invaluable for security leaders and CISOs, emphasising the importance of integrated data visibility. Role-based access ensures that the right personnel receive appropriate insights. Moreover, automated data collection guarantees real-time updates, allowing organisations to address vulnerabilities swiftly in the face of rapid cyber threats.
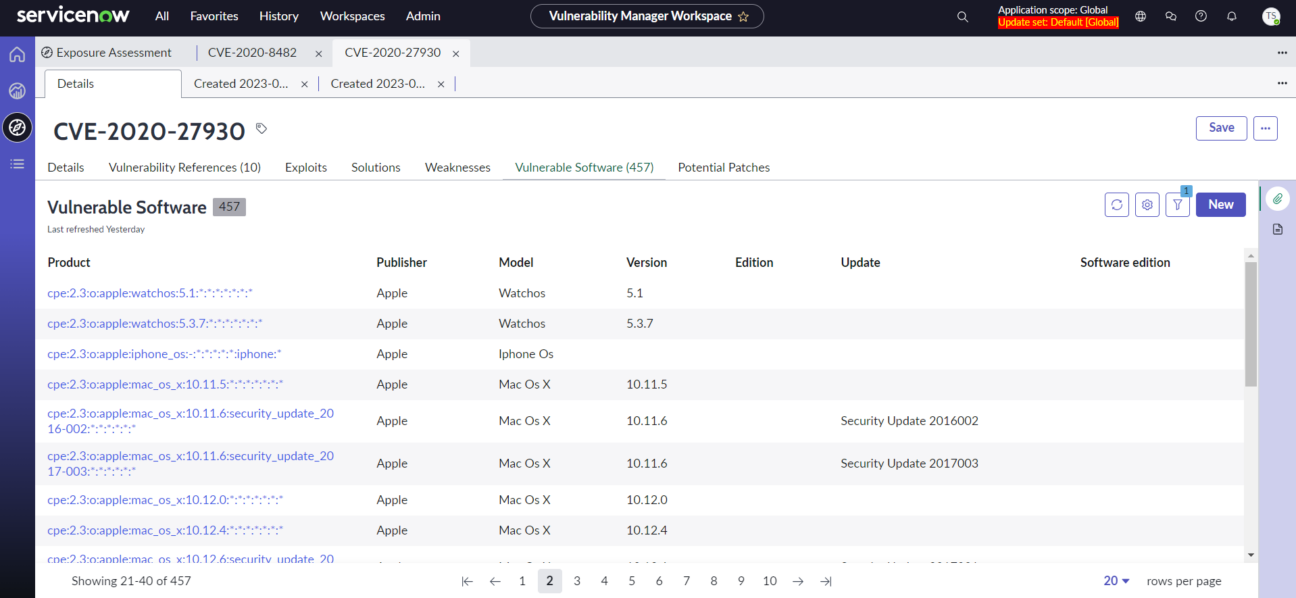
Zero-Day Vulnerability Insight
While speaking about the ServiceNow Vancouver release, we need to mention a new tool for evaluating assets’ vulnerability to emerging threats – Exposure Assessment. This advanced feature provides businesses with a granular view into impacted software assets with vulnerabilities listed in the CISA or NVD catalogues or by adding zero-day vulnerabilities to identify impacted assets.
By seamlessly navigating Exposure Assessment, analysts and managers can delve deep into affected systems and applications to understand the gravity of threats and formulate strategic responses.
Security Incident Response
The new ServiceNow release comes with some useful new features for Security Incident Response (SIR)
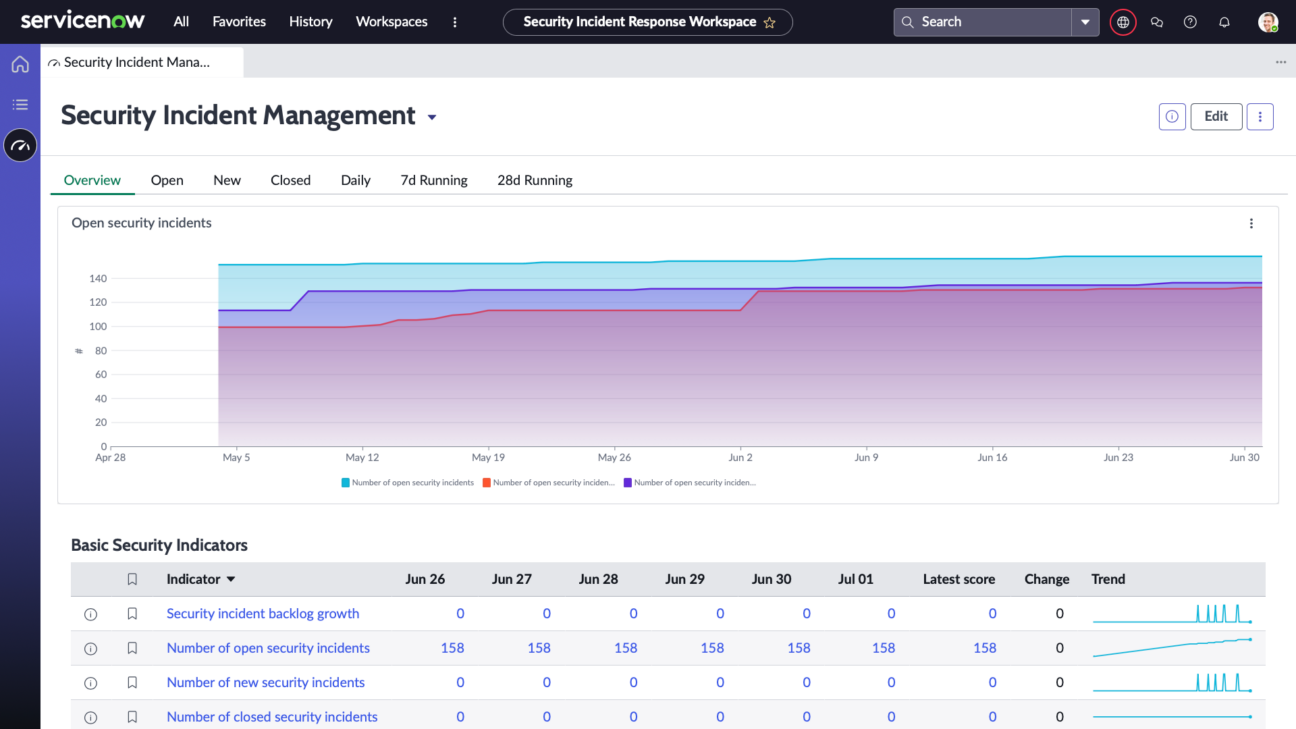
Viewing SIR Workspace Dashboards
In the Classic UI, there are a few standard dashboards available under the Homepage and Performance Analytics Dashboards that are available when the Performance Analytics for Security Incident Response plugin is installed. Thanks to the Vancouver release, it will be available in the new workspace under the SIR Dashboards section. CISO and Security Incident Manager overview dashboards migrated to an enhanced user interface.
The new interface delivers improved usability and ease of customisation. Now, you can:
- easily share insights with SOC leaders and other collaborative teams,
- get a single-pane-of-glass view of incidents, vulnerabilities, risk, and compliance metrics,
- see the operational dashboard for security & risk posture tracking,
- and utilise peer benchmarking of security and risk metrics to support budget planning.
Data Loss Prevention Incident Response
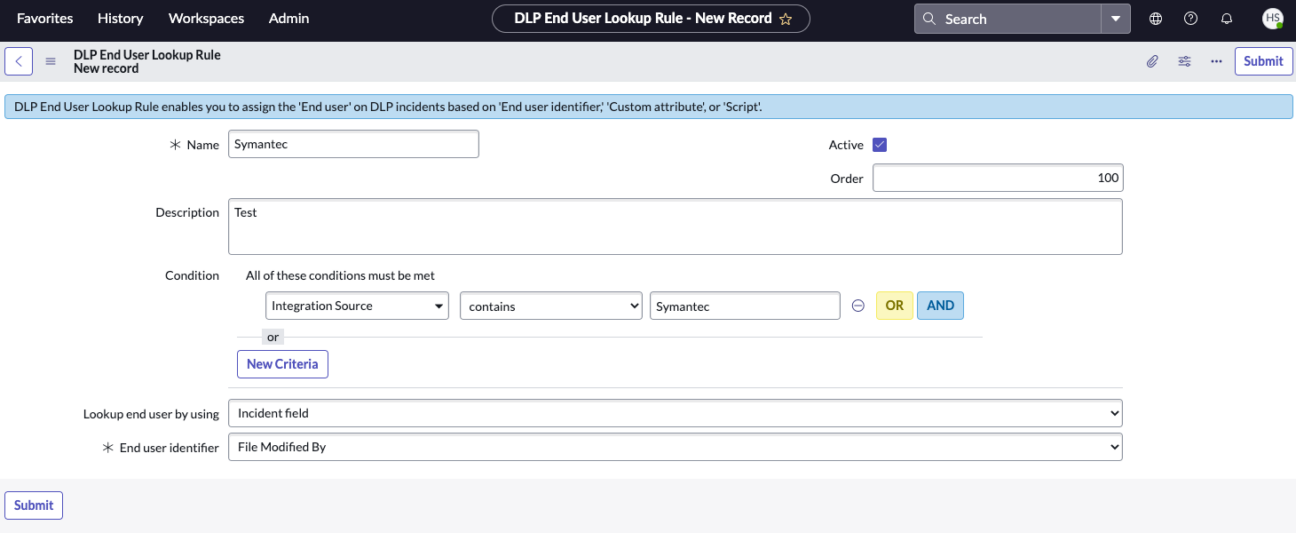
Configure end-user lookup rules
The DLP end-user lookup rule enables you to assign the end-user on DLP incidents based on the End-user identifier, Custom attributes, or Script fields respectively.
Create and manage user instructions template for DLP incidents
When an incident is assigned to the end-user, then the user might be required to know the additional instructions on how to:
- respond to the incidents,
- introduce the users to the terminology
- provide any additional information about the incident.
Creating and managing user instructions templates helps users provide accurate responses to DLP incidents and figure out the next steps.
Consolidate your DLP incidents
Automatically consolidate multiple incidents as child incidents under one parent based on custom criteria, e.g. some policy violations in a short period of time.
This new feature provides value by simplifying incident management, improving visibility, optimising resource allocation, and facilitating more effective incident response.
Configure Approval Rules
As a DLP admin, you can define the approval rules to grant consent on requests raised by end users to approve the advanced type of response option. You can also define multiple levels of approval from here. After configuring the approval levels, the users can approve or reject the assigned approval requests using the Data Loss Prevention Incident Response user workspace.

Certified ServiceNow Experts at your service
ServiceNow can empower your employees and clients with digitalized workflows, and Devoteam, as the #1 preferred Partner in the EMEA, is eager and ready to help make your digital transformation journey a success. Ready to see what we can bring to the table?


